May 2005 newsletter
Newsletter to the TCCC Membership
Welcome from the Chair - Joe Bumblis
Welcome to the May, 2005 TCCC newsletter. There are many exciting events to share with you - the TCCC membership. First, Klara Nahrstedt, Bin Yu and Jin Liang of the University of Illinois at Urbana Champaign {klara, binyu,jinliang}@uiuc.edu; and Mohan Kumar, University of Texas at Arlington {kumar@cse.uta.edu} submitted a conference report detailing the PerCom 2005 conference held on March 8-12, 2005 in Kauai, Hawaii. The text-only version is included in this newsletter for your review. An HTML version is now available on the TCCC web page (http://tab.computer.org/tccc).
Second, there are several conferences sponsored by the TCCC that are either in their “Call for Papers” phase, or in their “Call for Participation” phase. These conferences and their call dates are included below.
Third, in an effort to keep our membership updated of current and evolving technological standards, we present an overview articles by an expert on 802.11 LAN technology on the various current and future standards on high-speed WLANs.
I invite all of you to visit the TCCC web page and review the information currently available. As we progress through 2005, many additional offerings will appear for your educational and enlightenment activities.
IEEE Conference on Pervasive Computing (PerCom) Conference Report
The Third IEEE International Conference on Pervasive Computing (PerCom 2005) was held at the Sheraton Kauai Resort on the beautiful sunny Poipu beach of the Kauai Island, Hawaii.
As in the past, the conference activities focused on the emerging area of pervasive computing and communications aimed at providing an exciting platform and paradigm for all the time, everywhere services.
The conference call for papers received overwhelming response with 240 papers submitted.
The international technical program committee consisting of 53 researchers selected 31 top quality full papers and 8 concise contributions for oral presentations at the conference.
In addition, the conference comprised seven workshops, two keynote speeches, two panels and a demonstrations session.
Percom 2005 along with its seven workshops drew a total of 225 participants from 22 countries, over the five days of the conference events.
The main conference technical sessions started on Wednesday, March 9, with a keynote titled “Beyond global communications: The Active World” by Dr. Roy Campbell from University of Illinois at Urbana Champaign. Roy opened his talk with the observation that pervasiveness is a stepping stone to ubiquity, and the proliferation of appliances is leading to dramatic changes in how people communicate and interact. Then he introduced the concept of Active World and how the Gaia system schedules and allocates resources in Active Worlds to maximize human attention. Roy concluded his talk by pointing out the biggest challenges that lie in overcoming uncertainty in the environment, and in autonomic adaptation to human needs. The second keynote titled “Sensor Networking & Pervasive Computing” was given on Friday, March 11, by Dr. Sri Kumar from DARPA. Sri Kumar started with an historic overview of the field of sensor networks and pervasive computing. Of particular note was the use of sensor networks in National Defense. A DARPA funded project, SensIT, was discussed. The challenges faced and addressed included: ad-hoc, self-sustainable, low energy communication, and security issues. In conclusion, Sri emphasized that several advances have been made in the last few years, but many challenges still remain. One interesting question was about the environmental impact of deploying hundreds of sensor nodes: How do we clean up the sensors after their purpose has been accomplished? No solutions have been proposed for this problem.
Besides the keynotes, two panels, both moderated by Dr. Taieb Znati discussed two of the hot issues in the pervasive computing community. The first panel was on “Trustworthiness in Pervasive and Ubiquitous Environment” and the panelists were Roy Campbell, Mani Srivastava, David Wagner, Fabio Martinelli and Sri Kumar. Some interesting questions included “What are the solutions to risks?” and “Is there an inherent relationship between trust and usability?”. Klara Nahrstedt raised the issue of “cost of trust”, and the panel agreed on the importance of cost-benefit analysis and cost-trust balance. The second panel focused on “Challenges and Opportunities of Pervasive and Ubiquitous Computing in Health Care”. The panelists were Kathy J. Liszka, Jay Lundell and Loren Schwiebert. The panel dealt with long-term challenging research problems that need to be solved to enable ubiquitous care, and technological barriers that need to be addressed for the development of a large scale pervasive and ubiquitous infrastructure for healthcare. Long standing challenges including energy, security, real-time issues, reliability, and ergonomics of medical devices were explored. Many questions were discussed during the panel, such as problems of liability and standardization that are prohibiting the proliferation of many health care systems.
PerCom 2005 comprised eleven regular sessions, covering various aspects of pervasive computing, including pervasive applications, context and location management, middleware platforms, security, mobile services, pervasive devices, energy efficiency, service discovery, sensor and wireless networks, etc.
Some highlights include: Peng Zhou, et. al from University of Maryland and Rutgers University presented EZCab, which targets cab booking in dense urban areas using short range wireless communications;
Gopal Pingali et al. from IBM Research presented their work on a pervasive chronicling system that allows a user to record and share an entire lifetime of experiences into a pocket-sized storage device;
Matthias Grossmann from University of Stuttgart presented their Nexus platform, which is a scalable infrastructure for context data management.
Nexus integrates multiple specialized context servers rather a central server, and provides a single common interface (Augmented World Query Language) for performing a query across multiple servers.
The Mark Weiser best paper session was one of the highlights of the conference. The best paper award was presented to the paper, Sizzle: A Standards-based end-to-end Security Architecture for the Embedded Internet, authored by Vipul Gupta, Mathew Millard, Stephen Fung, Yu Zhu, Nils Gura, Hans Eberle, Sheueling and Chang Shantz. The paper presented a small-footprint implementation of the HTTPS stack called Sizzle, which needs less than 4kb of RAM. Sizzle uses Elliptic Curve Cryptography (ECC), which makes public key cryptography feasible on resource-constrained devices such as Berkeley motes, using substantially smaller key sizes, and resulting in faster computation and low power consumption. As a result, Sizzle on an 8-bit Berkeley Mica2 mote can complete a full SSL-handshake in less than 4 seconds which otherwise would take more than 10 seconds if RSA is used. The authors also gave a very interesting demonstration with their implementation of Sizzle on a Berkeley Mica2 mote used as a web server. A companion paper from the same authors analyzed energy consumption of the authentication and key exchanges using ECC and RSA.
The seven workshops focused on specific aspects of pervasive computing ranging from security in pervasive computing and communications (PerSec), middleware support for pervasive systems (PerWare), sensor networks and systems for pervasive computing (PerSeNS), context modeling and reasoning (CoMoRea), mobile peer-to-peer computing (MP2P), pervasive wireless networking (PWN), to pervasive learning (PerEL).
Elsevier’s new Journal on Pervasive and Mobile Computing (PMC) was announced at the conference. A special issue of PerCom 2005 selected papers will appear in Special Issue of PMC in early 2006.
The success of PerCom 2005 can also be attributed to the beautiful scenery of the Kauai Island and the accommodations offered by the organizing committee. An IBM student reception hosted by Gopal Pingali from IBM Research, and the NSF travel grant awards offered a great chance for students to attend PerCom 2005 and get to know each other. A grand conference luau was held on Thursday, March 10, on the beautiful lawns of the Sheraton Kauai Resort Hotel, where over 100 scholars and students joined in a nice evening of great food and signature shows from Kauai island.
Next year, the Fourth IEEE International Conference on Pervasive Computing will be held in Pisa, Italy on March 13-17, 2006. PerCom 2006 will provide a high profile, leading edge forum for researchers and engineers alike to present their latest research in the field of pervasive computing and communications.
Authors: Klara Nahrstedt and Mohan Kumar served as the program and general chairs respectively. Bin Yu and Jin Liang served as student volunteers.
Upcoming Conferences/Workshops Sponsored by the TCCC
The Second IEEE Workshop On Embedded Networked Sensors (EmNetS-II) May 30th-31st 2005, Sydney, Australia Call for Participation (http://www.cse.unsw.edu.au/~emnet/) [Co-sponsored with the University of New South Wale, National ICT Australia, CSIRO Australia, ARC (Sensor Networks), and TCCC at 25%]
The Second IEEE Workshop on Embedded Networked Sensors (EmNetS-II) will bring together researchers working in the broad area of embedded, networked sensors. The goal of the workshop is to promote community-wide discussion of ideas that will influence and foster continued research in the field. The workshop will provide a venue for researchers to present new ideas that have the potential to significantly impact the community in the long term, especially those exploring how practical considerations or novel application scenarios and requirements shape the design of these embedded and sensor networks.
The IEEE Conference on Local Computer Networks (LCN) - 30th Anniversary - November 15-17, 2005 Sydney, Australia Call for Papers (http://www.ieeelcn.org) [100% sponsorship by TCCC]
For the past 30 years, the IEEE LCN conference has been the premier conference on the leading edge of practical computer networking. LCN is a highly interactive conference that enables an effective interchange of results and ideas among researchers, users, and product developers. Over the years, LCN has tracked many developments from the local network to the global Internet and the World Wide Web. In 2005, we are targeting embedded networks, wireless networks, ubiquitous computing, heterogeneous networks, and security as well as management aspects surrounding them. We encourage you to submit original papers describing research results or practical solutions. Paper topics include, but are not limited to:
The following workshops are held in conjunction with LCN:
- WLN: 5th International IEEE Workshop on Wireless Local Networks http://www.cse.unsw.edu.au/~wln2005/
- 1st IEEE International Workshop on Performance and Management of Wireless and Mobile Networks: http://www.site.uottawa.ca/~boukerch/IEEE-perf.html
- The IEEE LCN Network Security workshop: http://www.cs.uvic.ca/~wkui/IEEE-WoNS.htm
‘From Around the TCCC ExCom’
The following Technical Brief was obtained through the efforts of Archan Misra, TCCC Un-tethered Network Technology Chair. The brief “A-V of IEEE 802.11 Wireless LAN Protocols” is offered by Dr. Sai Shankar N. Sai received his PhD degree from the department of Electrical Communication Engineering from Indian Institute of Science, Bangalore, India in the area of ATM networks. Since 2001, he has been with Philips Research USA, Briarcliff Manor, NY working in the area of Wireless LANs. He is an active contributor to and leader in various wireless LAN standards, such as 802.11e, 802.15.3 (Ultra-Wideband) and 802.11n.
A-V of IEEE 802.11 Wireless LAN Protocols
Sai Shankar N, Philips Research USA, sai.shankar@philips.com
Introduction:
Since the adaptation of IEEE 802.11 standard in 1997, it has been a remarkable success, which has seen its application range from data oriented computer communication to demanding multimedia applications such as voice and video. In response to growing applications and scarcity of limited unlicensed wireless spectrum, IEEE 802.11 has evolved over the years to use higher physical media transmission rates and cover additional unlicensed spectrum. The additional PHY layer protocols were developed to be compatible with the legacy IEEE 802.11 standard.
However, even as the wireless network was being widely deployed some weaknesses in the original MAC protocol got more scrutinized. For example, the WEP security mechanism in the protocol was shown vulnerable to attacks with the commonly available tools in as little as ten minutes. Secondly, in the European domains, there are some additional requirements on transmit power control and dynamic frequency selection which the original protocol did not address. Thirdly, looking at the future of the networking, real-time two-way and multimedia streaming applications took on increasing significance. While the IEEE 802.11 protocol was designed to provide good performance for data-centric applications, the legacy MAC protocol did not provide mechanisms to ensure QoS for the applications served. This article provides a simple overview of the current IEEE standard along with its amendments. Figure 1 illustrates the different amendments that have been already defined and the new amendments that would take few years to complete.
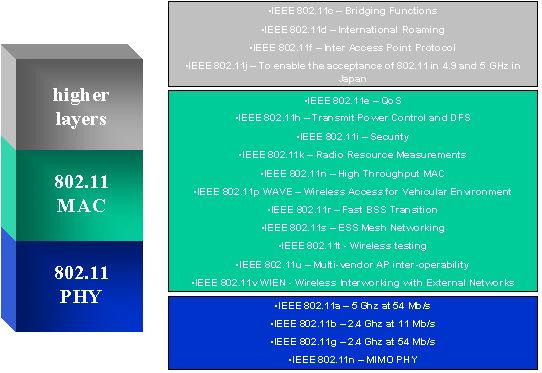 Figure 1: IEEE 802.11 standard and its amendments.
Figure 1: IEEE 802.11 standard and its amendments.
The IEEE 802.11 standard is an evolving standard as the legacy standard is continuously being amended to improve and address deficiencies mentioned above. Originally IEEE 802.11 standard was launched in 1997. The standard defined the MAC layer and three different physical layers. The original MAC is based on two coordination functions, namely, the Distributed Coordination Function (DCF) that is mandatory and the Point Coordination Function (PCF) that is optional. DCF is based on Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) and acknowledgement while the PCF works through polling. All of today’s 802.11 devices operate in the DCF mode only. In the DCF all devices listen to the channel to asses whether the channel is busy or not (this is also called as Clear Channel Assessment (CCA)) and waits for a random amount of time determined by the backoff process and then transmits the frame. If the frame is lost because of channel errors or collision, the transmitter doubles its backoff time value and then repeats the procedure outlined as before for a frame transmission.
IEEE 802.11 PHYSICAL LAYER
As mentioned earlier, the original MAC had three different physical layers that were based on Infra Red (IR), Direct Sequence Spread Spectrum (DSSS) and Frequency Hopping (FH). The IEEE 802.11 standard body added amendments in physical layer called IEEE 802.11a and IEEE 802.11b. The IEEE 802.11a operates in the 5 GHz band and has 8 different data rates ranging from 6 Mbit/s to 54 Mbit/s. The modulation is based on Orthogonal Frequency Division Multiplexing (OFDM). The IEEE 802.11b operates in the 2.4 GHz and has 4 different data rates ranging from 1 Mbit/s to 11 Mbit/s. In the year 2001, IEEE enacted a new amendment called as IEEE 802.11g that has the same modulation and data rates as IEEE 802.11a but operates in the 2.4 GHz. Currently IEEE is working on a new amendment called IEEE 802.11n that will use Multiple Input Multiple Output (MIMO) technology with a minimum data rate of 108 Mbit/s and the maximum exceeding 500 Mbit/s.
IEEE 802.11 MAC LAYER
Today, IEEE 802.11 can be considered a wireless version of Ethernet by virtue of supporting a best-effort service (not guaranteeing any service level to users/applications).
To enhance the performance of today’s WLAN, the IEEE 802.11 working group amended a new standard called IEEE 802.11e that would support QoS.
This is an extension of the current IEEE 802.11 legacy WLAN.
Since the WLAN operation in 5 GHz interferes with radars that are primary users of 5 GHz spectrum the IEEE 802.11 amended IEEE 802.11h that mandates the IEEE 802.11 WLAN to move out of the current frequency if the radar is detected.
This is called Dynamic Frequency Selection (DFS).
This amendment also includes Transmit Power Control (TPC), which defines the levels of power that the WLAN network or some stations in the network should use to minimize interference.
As already outlined in the introduction, the current Wired Equivalent Privacy (WEP) is broken and hence IEEE specified IEEE 802.11i that uses AES to get reliable data transfer, key exchange and ensure that the protocol is not prone to eavesdropping.
In order to determine the optimal Access Point (AP) for association and the load on each BSS, IEEE 802.11 amended IEEE 802.11k that enables measurement of radio resources.
IEEE 802.11n was amended to look for ways to enhance IEEE 802.11e to get throughputs starting from 108 Mbit/s.
This standard is designed to use MIMO technology and is backward compatible with IEEE 802.11.
To enable communication when devices using WLANs are in vehicles traveling in highways at speeds of 60 miles per hour or in trains traveling at 200 kilometers per hour, IEEE 802.11p enables inter vehicle communication as well as communication between vehicles and road side devices.
This amendment is in progress and will be used in 5.8 GHz band in North America.
IEEE 802.11r was established in order to enable seamless roaming between different WLAN networks, minimize the handoff latency and ensure QoS while performing handoff.
In order to have a wireless mesh technology wherein the entire city can have a wireless connectivity without having to engineer to place the APs optimally, IEEE 802.11 amended the IEEE 802.11s.
This would support broadcast, multicast and unicast data transfers at very high rates.
IEEE 802.11t was amended in order to test the performance of different applications running over IEEE 802.11.
This would device a common set of accepted performance metrics and measurement methodologies.
IEEE 802.11u was formed to enable inter working with other wireless networks that would include frame exchanges at the protocol level and any primitives that would be required for this functionality at the higher layer level.
IEEE 802.11v was formed to enable management of attached stations in a centralized or in a distributed fashion (e.g. monitoring, configuring, and updating).
This is different from IEEE 802.11k that does only measurements and not configuring and updating of any devices.
HIGHER LAYER FUNCTIONALITY
IEEE 802.11c provides required information to ensure proper bridge operations. This is used by product developers when developing access points. When 802.11 first became available, only a handful of regulatory domains (e.g., U.S., Europe, and Japan) had rules in place for the operation of 802.11 wireless LANs. In order to support a widespread adoption of 802.11, the IEEE 802.11d task group has an ongoing charter to define PHY requirements that satisfy regulatory requirements in additional countries. This is especially important for operation in the 5 GHz bands because the use of these frequencies differ widely from one country to another. The existing 802.11 standard does not specify how access points should communicate among themselves to support users roaming from one access point to another. Consequently, when roaming, baccess points from different vendors would frequently not inter-operate with one another. IEEE 802.11f thus specifies an inter-access point protocol that provides the necessary information that needs to be exchanged to enable efficient roaming. With the opening of new wireless bands for indoor, outdoor, and mobile use in Japan, the IEEE has approved an amendment to IEEE 802.11 to support the new spectrum and their designated applications. The amendment, IEEE 802.11j, will enable WLAN vendors to offer wireless products that adapt to new frequencies, different channel widths, and operating parameters.
Please do not hesitate to contact me or any of the ExCom members if you have any questions or concerns regarding TCCC activities. In particular, we would love to have your feedback on what you would like to see in future newsletters, and the online publications area of the TCCC web page with suggestions ranging from tutorial-style articles on emerging technical areas by experts to original research articles to reports on ongoing TCCC-related activities in different IEEE regions. Your feedback will enable us to serve our common interests in a more productive way.
Thank you,
Joe Bumblis
Chair, TCCC